- Home
- Fundamentals of Email Marketing
- How to Choose the Most Secure ...

One morning in 2014, a Sony Pictures executive clicked on an email that looked routine—a request to verify his Apple ID. It was a phishing email, expertly crafted to appear authentic. Within days, hackers had leveraged that one click to infiltrate Sony’s network. Posing as a legitimate Apple login page, the scam prompted employees to enter their passwords, which attackers then used to breach Sony’s systems. The result was catastrophic: a digital heist that wiped servers and spilled Sony’s secrets to the world.
This dramatic episode underscores a simple truth: email security is critically important in today’s world. When an email account gets compromised, the fallout can be devastating, as seen in Sony’s case. In 2025, with email still the backbone of global communications, choosing the most secure email provider is an absolute necessity.
So, if world leaders and corporations aren’t safe, how can the rest of us be? In this article, we talk about email encryption software, email providers, and their features that make email communication, if not bulletproof secure, at least reliable enough to keep your data safe.
Anatomy of an Email Hack
How do email hacks happen?
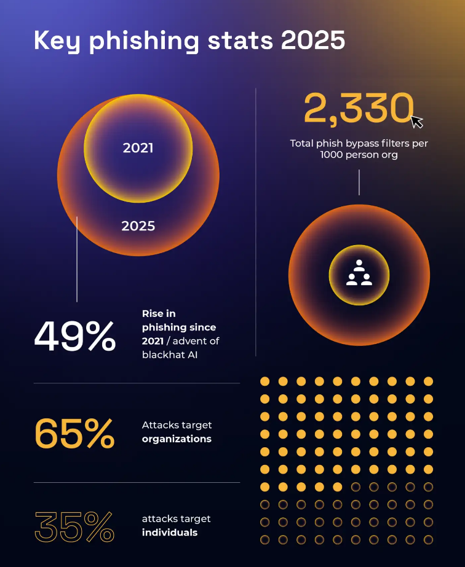
In many cases, it’s not some high-tech exploits but rather age-old tricks that break in. The most common culprit is phishing. In fact, phishing accounts for up to 90% of cybersecurity breaches worldwide. Hackers know that a carefully crafted email—be it a bogus security alert, a wire transfer request, or a message like “Your account was compromised, click here to secure it”—can bypass even the best firewalls by targeting the most unpredictable variable: human trust.
Another weak link is poor password hygiene. Weak or reused passwords make it easy for attackers to break in by guessing or using databases of leaked passwords from other sites. And when emails are sent or stored without strong encryption, they become low-hanging fruit; anyone who intercepts the traffic or breaches the server can read everything in plain text. In short, email often represents a single point of failure: crack one account, and you could gain entry to a whole network.
Real-world email hack examples
Real-world hacks illustrate how one compromised inbox can snowball into a crisis. The 2016 U.S. election hack is a very telling example of that. A phishing email tricked an aide of Clinton campaign chairman John Podesta into thinking it was a legitimate security alert. As a result, Russian hackers were given prolonged access to the DNC computer system. The attackers stole around 60,000 of Podesta’s private Gmail messages—correspondence that was later dumped onto WikiLeaks for the world to scrutinize. Those leaked emails fueled headlines for months, altering the political conversation during a presidential race.
Another notorious example was the breach of Stratfor, a global intelligence firm. In December 2011, members of the hacktivist collective Anonymous infiltrated Stratfor’s systems and stole millions of internal emails. WikiLeaks later published over 5 million of these messages, revealing Stratfor’s dealings and client information to the public.
If even a high-powered security consultancy couldn’t keep its emails safe, it’s a stark reminder that email is often the weakest link. From corporate boardrooms to campaign war rooms, a single email breach can lead to complete chaos. These incidents highlight why robust email security is so crucial.
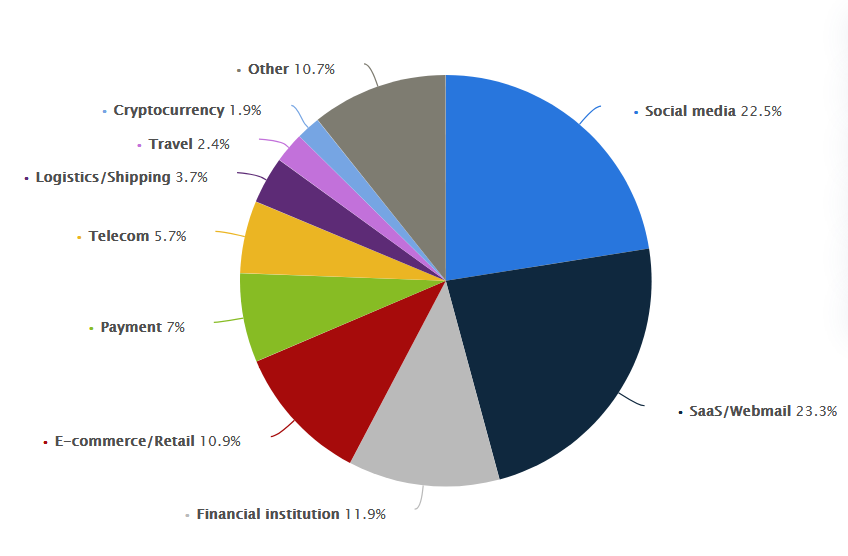
Industries most impacted by phishing attacks in the end of 2024
What Makes an Email Provider Secure?
Not all email services are created equal. So, what is the safest email provider made of? In evaluating the most secure email providers, experts look for a few non-negotiable features that separate truly secure platforms from the rest. Here are the key ingredients that define a secure email service today:
✅ End-to-end encryption (E2EE): This is the foundation of any encrypted email service. With E2EE, your message is locked by your device before sending and can only be unlocked by the intended recipient. Nobody in between—not your email provider, not even the government—can read the content. Even if hackers intercept the message or break into the provider’s servers, all they see is ciphertext gibberish.
✅ Zero-access architecture: Hand-in-hand with E2EE is a zero-knowledge approach. This means the provider itself has zero access to your decrypted emails or password. Your data is stored encrypted in such a way that even the company can’t read it. In practice, this protects you in case the provider’s servers are breached or subpoenaed; there’s simply nothing meaningful to hand over. Secure providers often encrypt emails at rest on the server with keys only you possess.
✅ Open-source code & audits (transparency): Trust is good, but verification is better. The most secure email providers reinforce trust by embracing transparency. Transparency and auditability mean there are no secret backdoors, and anyone can inspect how the email encryption service works. Some providers also undergo third-party security audits and publish transparency reports about government data requests. Being open and honest about security (and failures, if they happen) is a hallmark of a provider you can trust with your data.
✅ Two-factor authentication (2FA): If you’re evaluating what is the safest email provider for you, make sure robust 2FA is part of the package. By requiring a second step—like a one-time code from your phone or a hardware key—even a stolen password won’t be enough for an attacker to break in. This extra layer prevents many hacking attempts. The best secure email services support modern 2FA methods (authenticator apps, U2F keys, etc.), and some even offer innovative options like login via physical USB keys for maximum protection.
✅ Metadata protection: Even when email contents are encrypted, metadata (like sender, recipient, subject line, and IP addresses) can reveal a lot. That’s why top secure email providers take steps to minimize metadata exposure. The less information leaked in transit or in the email header, the better. A truly secure email service handles not just message content encryption but also shields the surrounding data whenever possible.
✅ Jurisdiction & privacy laws: Where your email provider is based matters too. Local laws determine how easily governments or third parties can demand access to your data. Many of the best secure email services deliberately operate in privacy-friendly jurisdictions. That said, jurisdiction isn’t a free pass—but it can offer an extra layer of legal defense. When choosing a provider, consider if their country has a track record of defending privacy (or conversely, laws that might conflict with it).
Top Secure Email Providers (Comparative Overview)
ProtonMail (Proton)
ProtonMail, developed by CERN scientists and based in Switzerland, has become one of the most trusted names among secure email providers. With default end-to-end encryption and a strict zero-access architecture, Proton ensures that no one—their own servers included—can read your emails. It uses open-source cryptographic libraries based on PGP and supports self-destructing messages, password-protected emails, and address aliases. ProtonMail operates under Switzerland’s robust privacy laws and publishes regular transparency reports. Its codebase is open source, allowing for external audits.
Tutanota
Tutanota, headquartered in Germany, is known for taking email encryption a step further. Unlike ProtonMail’s PGP foundation, Tutanota developed its own encryption protocol that secures not only the body and attachments of your emails but also the subject line, metadata, calendar, and contacts—by default. Its zero-knowledge infrastructure ensures that your keys and data are accessible only to you. Tutanota is also fully open source and prides itself on independence from Big Tech ecosystems, even creating its own captcha system to avoid using Google’s. All IP addresses are stripped from headers, and encrypted search allows users to search through encrypted data without compromising security.
Mailfence
Mailfence, based in Belgium, strikes a balance between security and compatibility. It supports OpenPGP for end-to-end encryption and digital signatures, allowing smooth communication with users of other PGP-compatible platforms. Unlike ProtonMail and Tutanota, which use proprietary systems for secure external communication, Mailfence gives you full control over your encryption keys and offers a built-in keystore. While the platform itself is not open source, Mailfence relies on open standards and has published its stance on government data requests, emphasizing transparency. Because Mailfence can technically access your inbox (unless you encrypt with PGP), it trades off a bit of privacy for convenience—like password resets.
Posteo
Posteo is a privacy-first email service from Germany that emphasizes anonymity, sustainability, and strong transport security. Unique among secure providers, Posteo allows fully anonymous sign-up and payment—even accepting cash by mail. It doesn’t require any personal data and strips IP addresses from emails, making them untraceable. Though it doesn’t offer built-in end-to-end encryption, Posteo supports PGP and integrates easily with tools like Mailvelope for those who want that extra layer. It also provides an opt-in feature that encrypts your entire mailbox at rest using a user-supplied password, making stored data unreadable even to Posteo. While not fully open-source, it runs on open standards and has published detailed information about its encryption practices.
CounterMail
CounterMail, based in Sweden, is the go-to choice for users seeking maximal security, even at the hardware level. It employs strong end-to-end encryption using OpenPGP with 4096-bit keys and performs all encryption/decryption on your local device. What sets CounterMail apart is its use of diskless servers—web servers with no hard drives that boot from read-only CDs—making it nearly impossible for data to be physically recovered in the event of a breach. It also strips IP addresses from headers and does not log user activity.
CounterMail supports secure login via USB key-based two-factor authentication and includes an encrypted password manager called Safebox. While its interface is somewhat dated and the service is entirely paid (no free plan), CounterMail’s architecture offers some of the strongest defenses against intrusion and surveillance.
What Is the Most Hacked Email Provider?
With all the insights provided, you might be wondering which email services hackers are actually breaking into the most. The answer requires some nuance. Historically, the unfortunate title of “most hacked” could be given to the largest, most widely used providers, simply because they present the biggest target and yield the most data when breached. In terms of ongoing attacks, Gmail (Google’s email service) and Microsoft’s email platforms (Outlook.com and Office 365 for businesses) are prime targets today due to their ubiquity. In fact, Gmail is often cited as the most targeted email service—one report noted that hacking attempts against Gmail accounts increased by 243% in early 2024. It’s not that Gmail is poorly secured (Google invests heavily in security), but with over 1.5 billion users, it’s a huge attack surface.
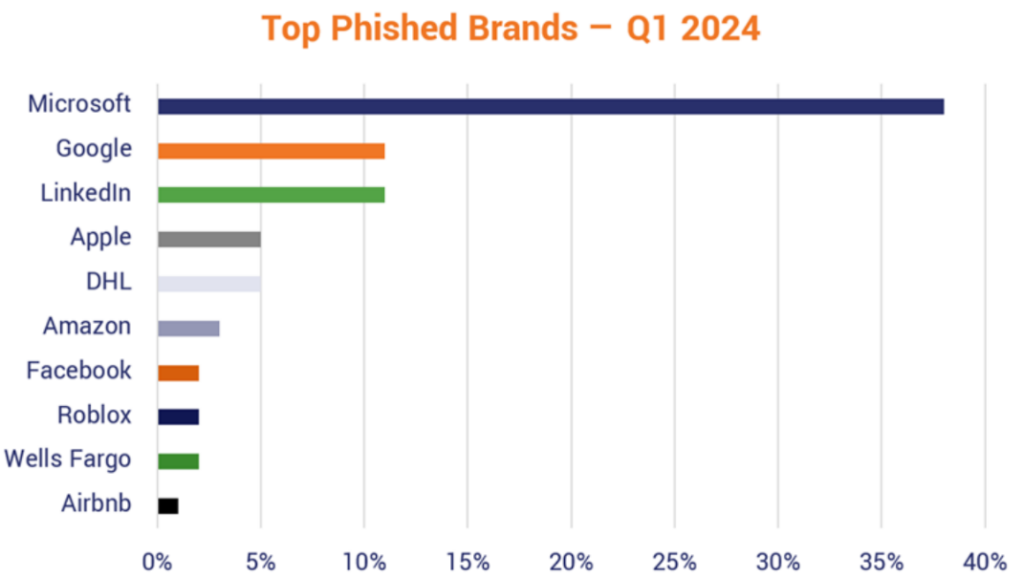
Microsoft’s email services are equally—if not more—under siege, especially in the corporate realm. Microsoft 365 (formerly Office 365) is used by millions of organizations worldwide, which makes it a favorite target of phishing and business email compromise scams. In late 2023, a cybersecurity report found that Microsoft was the #1 most impersonated brand in phishing attacks worldwide, accounting for about one-third of all brand phishing attempts.
It’s important to note that being frequently targeted isn’t the same as being insecure. The high numbers of incidents reflect the relentless effort attackers put into tricking users of these services. In summary, the most hacked email providers are the household names—Gmail, Yahoo, Outlook—not necessarily because their security is the weakest, but because that’s where the people (and the data) are.
Conclusion: Privacy Is a Necessity, Not a Luxury
Email started as a convenient communication tool and has evolved into a linchpin of our digital lives and a prime target for attackers. Choosing the most secure email provider you can is one of the simplest yet most impactful steps toward protecting your digital privacy. The secure email services highlighted above exist because of lessons learned from countless hacks and leaks—they are built to prevent the next Sony, the next DNC, or even the personal equivalent of those disasters from happening.

