- Home
- Fundamentals of Email Marketing
- All About Email Protocols: Sen ...

SMTP. API. IMAP. POP3. DMARC. A few more of these technical abbreviations, and some less experienced email marketers might be on the brink of a meltdown or a heart attack. However, we promise: once you see past the technical-sounding jargon of the field of email authentication, the use of it becomes pretty evident. In the end, email protocols fall into four main categories—sending, receiving, securing, and authenticating. Once you know which group a protocol belongs to, its purpose becomes much easier to grasp.
In this article, we tried to provide email marketers such as yourself with the right information on how to handle the technical aspects of email sending. Knowing these foundations can help with troubleshooting and with better understanding why some campaigns work—and others don’t. Especially in the light of increased phishing attacks and growing security scrutiny, the topic will only continue to gain importance.
Core Email Protocols (Transmission & Retrieval)
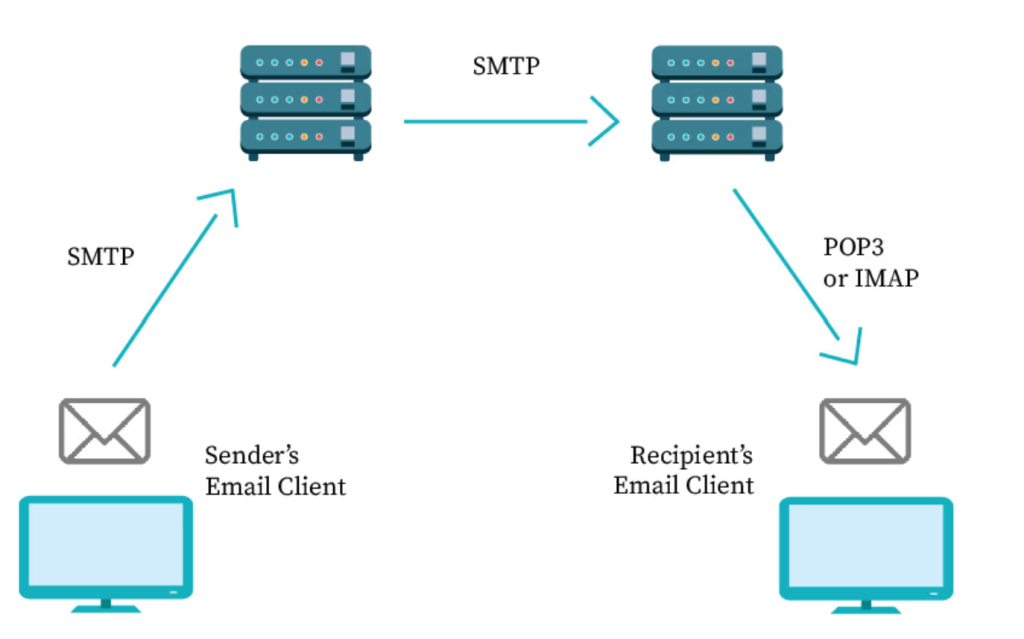
Email protocols can, in fact, be compared with the rules of the road that allow emails to move between servers and devices. Among all the different protocols that exist, three stand at the core of email transmission and retrieval: SMTP, POP3, and IMAP. Together they cover the sending, downloading, and syncing of emails, which constitutes the entire cycle of how messages move.
SMTP (Simple Mail Transfer Protocol)
Every email begins its journey with SMTP. This protocol handles the actual “sending” process: it takes your message from your email client and delivers it to the recipient’s mail server. It does this by breaking the message into a structured set of commands and data that mail servers can understand, transmitting it step by step from one server to another until it reaches its destination. Once it arrives at the recipient’s server, other protocols (like POP3 or IMAP) step in to make sure the message appears in the inbox.
POP3 (Post Office Protocol version 3)
POP3 was one of the earliest solutions for checking email, and its philosophy is simple: download everything from the mail server and keep it on your device. Once an email is downloaded, it often disappears from the server, meaning the message essentially “lives” on the device where you retrieved it. This works well if you mostly use one computer, since it guarantees offline access. But the downside is obvious in today’s world of multiple devices—if you open your email on your laptop, you may not see the same messages on your phone.
IMAP (Internet Message Access Protocol)
IMAP was designed to address the limitations of POP3 in a multi-device world. Instead of pulling messages off the server, IMAP keeps them stored in the cloud and syncs them across all devices. This means if you read an email on your phone, it also shows up as “read” on your laptop or tablet. IMAP also supports folder organization, message searching, and partial downloads, making it much more aligned with how we interact with email today, which makes it crucial for contemporary email marketing.
Security Protocols
When you send an email, it passes through multiple servers and networks before it arrives. Along the way, it can be vulnerable to interception if it’s not protected. This is the reason why we need security protocols, such as SSL, TLS, and STARTTLS.
SSL/TLS—encryption for SMTP, POP3, and IMAP
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are the core of secure email transmission. While SSL was the original standard, TLS is its modern, stronger replacement. In practice, these protocols create an encrypted tunnel between your device and the email server, so no one can “peek inside” your messages as they move across the internet.
What’s in it for marketers? For marketers, the benefit goes beyond technical safety. TLS encryption helps protect sensitive customer data (from addresses to billing confirmations), which helps to maintain trust. Many modern email providers automatically use TLS when sending mail via SMTP or retrieving it through POP3 or IMAP, which means you don’t need to configure much yourself.
STARTTLS—upgrading plain connections to secure ones
STARTTLS is a little upgrade option. If an email server starts out using an unencrypted connection, STARTTLS steps in to “upgrade” it to a secure one mid-session. It’s not a protocol in itself but rather a command layered onto existing protocols like SMTP, POP3, and IMAP. In most modern email systems, this upgrade happens automatically whenever both servers support it, but administrators can also configure it manually if needed.
Why does this matter? Because it means even older systems can adopt stronger protection without needing to be rebuilt. For marketers, it ensures your carefully designed campaigns don’t just look good but also travel safely, which is of the utmost importance for customer trust in industries handling sensitive data like finance or healthcare.

Authentication & Anti-Spoofing Protocols
Email isn’t only vulnerable to interception but can also be affected by impersonation. Attackers tend to send fraudulent messages that look like they come from legitimate brands. The role of email authentication protocols is to perform identity checks to make sure that the sender is really who they claim to be.
Why authentication matters
Authentication protects both businesses and users. For businesses, it prevents brand damage: nothing ruins trust faster than your customers receiving fake support emails that steal their passwords. For users, it ensures the messages they open are genuinely from the sender they trust. In other words, authentication directly influences deliverability and reputation. Email providers like Gmail or Outlook are far more likely to route your messages to the inbox if they can confirm you’re legitimate.
SPF—sender verification
SPF (Sender Policy Framework) tells receiving mail servers which IP addresses are allowed to send emails on behalf of your domain. If an email comes from an unauthorized server, it gets flagged or rejected. For marketers, properly configured SPF records reduce the risk of spammers hijacking your brand identity and protect your sender reputation.
DKIM—message integrity
DKIM (DomainKeys Identified Mail) takes things further by attaching a digital signature to each email. This signature proves the message hasn’t been tampered with in transit. For marketers DKIM ensures that the content of their emails was not affected in the process and reaches subscribers exactly as they were written.
DMARC—enforcement and reporting
DMARC (Domain-based Message Authentication, Reporting, and Conformance) ties SPF and DKIM together and adds a layer of policy. It tells receiving servers what to do if an email fails authentication—whether to quarantine it, reject it, or let it through. It also provides reports so you can see if someone is trying to spoof your domain. For marketers, DMARC is both a shield and a feedback tool: it protects your subscribers from phishing and gives you insights into who might be abusing your brand name.
Modern Access Protocols
While SMTP, POP3, and IMAP remain the core foundations of email, the way people access their inboxes has changed. Today, many users don’t configure a desktop client at all—they simply log into Gmail, Outlook, or Yahoo through a browser. Similarly, apps and services increasingly rely on APIs rather than old retrieval protocols. These modern access methods make email much easier to use.
Webmail (HTTP/HTTPS)—Gmail, Outlook, Yahoo, etc.
Webmail is the most familiar form of email access for most users today. Instead of configuring a client, you just open a browser and log in. Emails are still delivered over standard web protocols—HTTP or, more commonly, HTTPS for secure connections. The advantage is convenience: your inbox is always accessible from any device with an internet connection. For marketers, webmail dominance means that campaigns need to have responsive design to look and perform well inside browser-based clients.
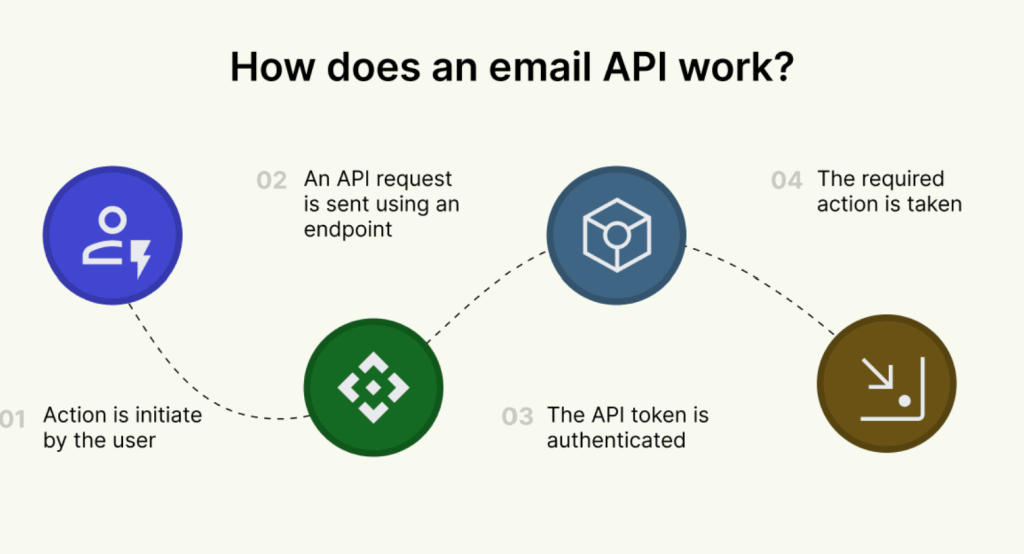
API-based access (e.g., Gmail API, Microsoft Graph)—increasingly used by apps instead of IMAP/POP3
In recent years, email providers have introduced APIs as a faster and more flexible way for apps to access inboxes. Gmail API and Microsoft Graph, for example, allow third-party tools to fetch, send, or organize emails without relying on IMAP or POP3. The introduction of APIs has allowed for the improvement of the overall quality of the email experience, and now many marketing platforms integrate directly with APIs for analytics, automation, and deliverability tracking.
Specialized or Provider-Specific Protocols
While protocols might seem universal, that is not quite true. Over time, different industries and providers have experimented with their own standards and settings. While many of these have faded into history, they remain important to mention because they illustrate how fragmented email once was and why today’s transition toward standardization matters so much.
Legacy and niche protocols (e.g., X.400)
Before SMTP and IMAP became the universal choice, there were alternatives like X.400. This system was once common in government and large enterprises, valued for its reliability but notorious for its complexity. Although it has largely disappeared, it shows that today’s email standards were not always the only option.
Provider adaptations (e.g., AT&T email settings)
Some providers introduced unique settings or small adjustments to the standard protocols. For example, AT&T email, which is often used by customers of AT&T’s internet and telecommunications services in the U.S., has its own email configuration requirements. For marketers, these variations sometimes create challenges when delivering campaigns to customers on those systems.
Transition toward standardization
The long-term trend has been clear: providers are moving toward universal standards such as SMTP, IMAP, and API-based access. This shift reduces compatibility problems and ensures emails display consistently across platforms. For marketers, this is a positive development, as it makes campaign testing more predictable and prevents surprises when targeting audiences using different providers.
How Email Protocols Work Together
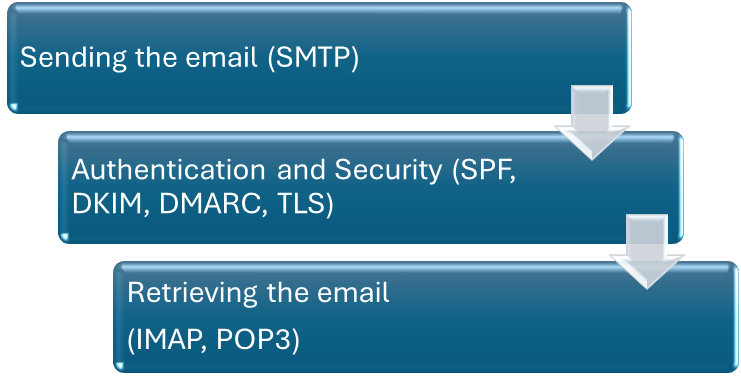
Each email protocol plays a role in the overall journey of a message. No single protocol covers the entire process; instead, they interact in sequence to make sure messages are sent, verified, protected, and then retrieved.
How does the typical flow of an email look?
When you hit “send,” the message first goes through SMTP, which handles transmission between your client and the recipient’s mail server. Along the way, it passes through authentication and security protocols such as SPF, DKIM, DMARC, and TLS to ensure the sender is legitimate and the message hasn’t been altered. Finally, when the recipient checks their inbox, IMAP or POP3 retrieves the email, depending on how their system is configured.
The process of email travelling through protocols: from sending to retrieving
The Future of Email Protocols
Email is far from static. As digital communication grows more complex and security threats more sophisticated, the underlying protocols are evolving too. The future points toward stronger protection and modern access methods that reflect how people now use email.
- Shift toward stronger encryption and zero-trust models
Encryption is becoming the default rather than the exception. Many providers are adopting zero trust principles, meaning no server or connection is trusted automatically and every step requires verification. This helps protect against increasingly advanced interception and spoofing attempts.
- Growing importance of DMARC compliance
What started as an optional best practice is quickly becoming a necessity. Email providers are enforcing DMARC more strictly, and organizations that fail to comply risk having their campaigns rejected or sent to spam.
- API-driven email access over legacy protocols
Just as webmail replaced desktop clients for many users, APIs are steadily replacing legacy access protocols like IMAP and POP3. For businesses, this means more reliable data handling and more seamless campaign execution.
To Sum Up
Knowing about different email protocols—the ones that form the backbone of email today, those that are slowly fading out, and the new approaches that are beginning to take their place—is crucial for having an overall understanding of how the entire email ecosystem operates.
Writing good copy will always be a crucial part of a successful email marketing campaign, and an increasing understanding of the technical foundations—plus the ability to comply with the requirements on this side—will continue to separate decent email marketers from outstanding ones.

